Why pay breach fines?
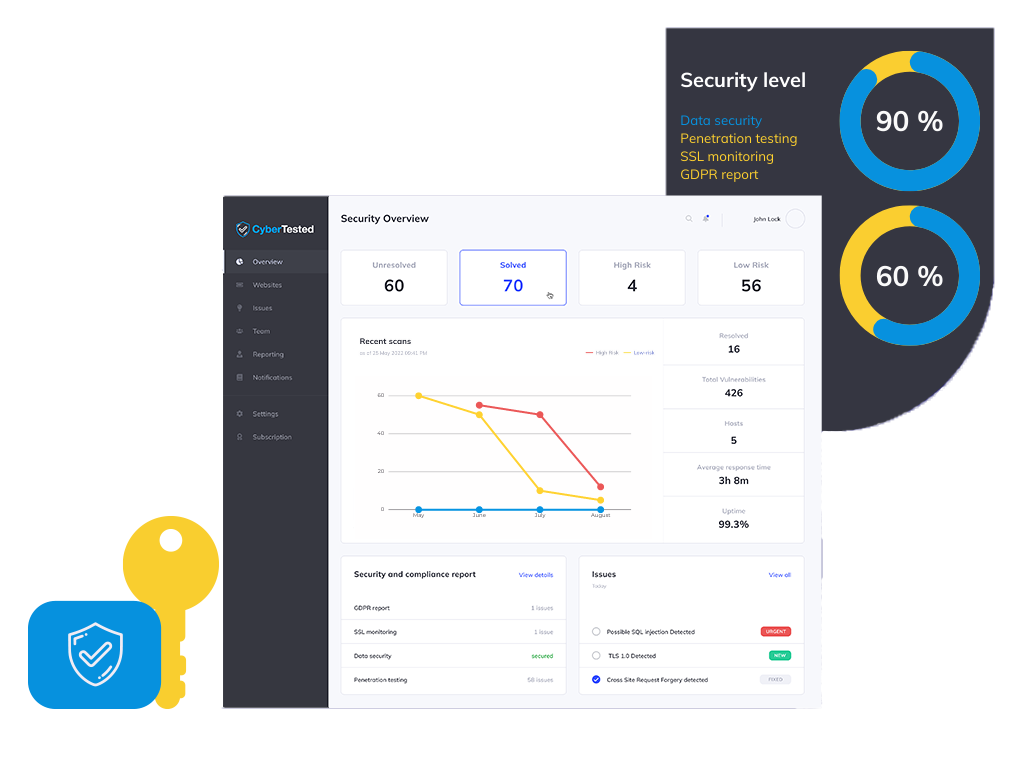
AI-Powered PenTesting for Every Security Risk
At CyberTested, our AI continuously tests and monitors your digital infrastructure to prevent security breaches and ensure regulatory compliance. We protect your business and customer data without draining your resources.